
WP Bakery WordPress Vulnerability Affects Millions of Sites via @martinibuster
Researchers discovered a vulnerability in WP Bakery page builder that allows an attacker to inject malicious JavaScript into pages and posts. The vulnerability allows an attacker to inject code into pages and posts that then attacks site visitor browsers.
Authenticated Stored Cross-Site Scripting (XSS) Vulnerability
Cross-site scripting vulnerabilities are characterized by an attacker gaining the ability to target the browsers of visitors through the use of malicious scripts that were surreptitiously placed on a website.
XSS attacks are among the most prevalent type of vulnerabilities.
This specific attack is called an Authenticated Stored Cross-Site Scripting Vulnerability. A Stored XSS vulnerability is one in which a script is placed in the website itself by an attacker.
But this is an Authenticated Stored XSS vulnerability, meaning that the attacker must have website credentials in order to execute the attack.
This makes it less of a critical risk because it requires an attacker to take the extra step of acquiring credentials.
Related: How Does Website Security Affect Your SEO?
WP Bakery Authenticated Stored XSS vulnerability
This specific WP Bakery vulnerability requires that the attacker obtain contributor or author level posting credentials to a website.
Once an attacker has the credentials they are able to inject scripts on any posts or pages. It also gives the attacker the ability to alter the posts created by other users.
This vulnerability was composed of multiple flaws.
The flaws allowed the injection of HTML and JavaScript into a credentialed users posts or pages and also to those of other authors. There was also another specific flaw that targeted buttons that had a JavaScript functionality attached to it.
Advertisement
Continue Reading Below
According to WordFence:
“The plugin also had custom onclick functionality for buttons. This made it possible for an attacker to inject malicious JavaScript in a button that would execute on a click of the button. Furthermore, contributor and author level users were able to use the vc_raw_js, vc_raw_html, and button using custom_onclick shortcodes to add malicious JavaScript to posts.”
WP Bakery Page Builder 6.4 and Under Are Affected
The vulnerability was discovered in late July 2020. WP Bakery issued a patch in late August but other problems still remained, including in a second patch issued in early September.
The final patch that closed the vulnerability was issued on September 24, 2020.
Plugin software developers publish a changelog. The changelog content is what shows up in the WordPress admin plugin area that communicates what an update is about.
Advertisement
Continue Reading Below
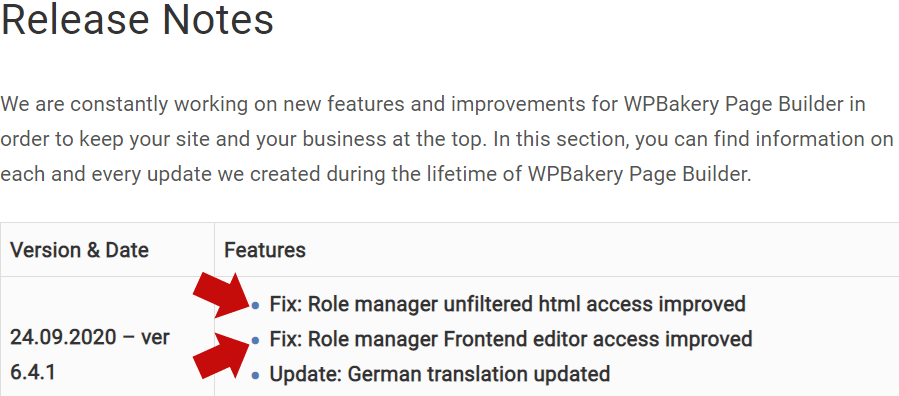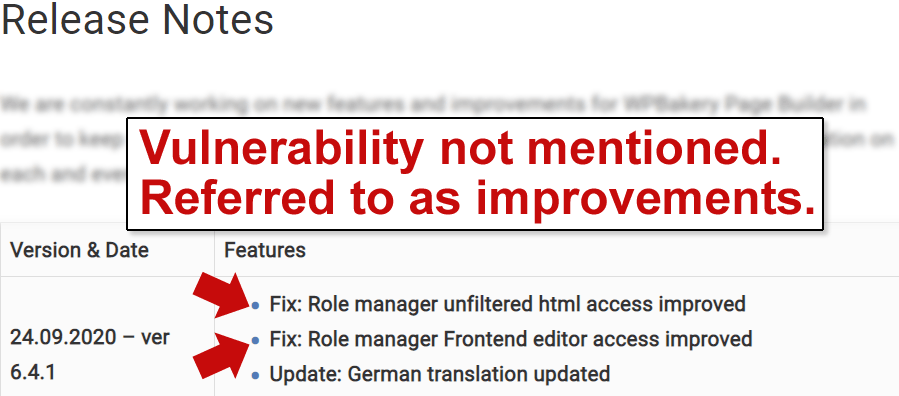
Unfortunately, WP Bakery’s changelog does not reflect the urgency of the update because it does not explicitly say that it is patching a vulnerability. The changelog refers to the vulnerability patches as improvements.
Screenshot of WP Bakery Page Builder Changelog

Advertisement
Continue Reading Below
The WP Bakery Page Builder plugin is often included in themes. Publishers should check their plugins and make sure they the latest and safest version which is 6.4.1.
Citations
Vulnerability Exposes Over 4 Million Sites Using WPBakery
WP Bakery Page Builder Changelog
https://kb.wpbakery.com/docs/preface/release-notes/





